In response to growing threats to IoT devices, RX 32-bit microcontrollers (MCUs) provide security solutions that will protect against threats throughout the lifecycle of IoT devices, from autonomous security and the design phase to end-of-life.
Features
Renesas' proprietary security engine, TSIP (Trusted Secure IP), enables autonomous security for IoT endpoint devices
IoT devices that are located in a network environment are constantly exposed to a variety of threats. However, if the IoT endpoint device itself is secure, it can protect itself from threats and prevent malicious and unauthorized behavior, even in an unsafe network environment. RX has strong security technology using Renesas' proprietary security engine, TSIP (Trusted Secure IP), and provides autonomous security for IoT endpoint devices.
For information on Renesas IoT security solutions, please refer to Renesas IoT Security.
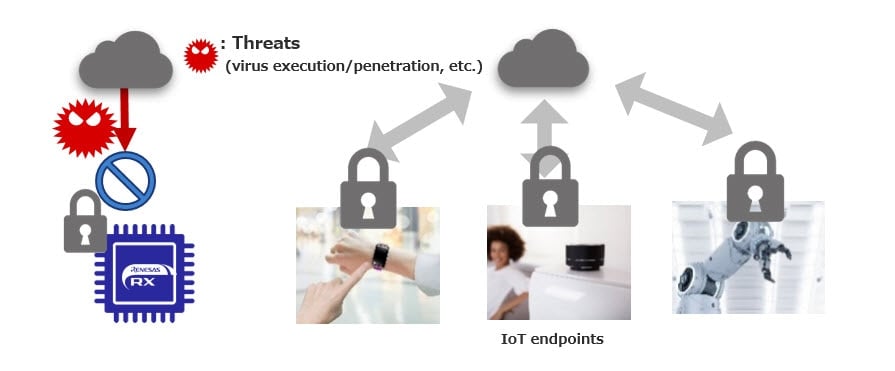
RX Security Solutions
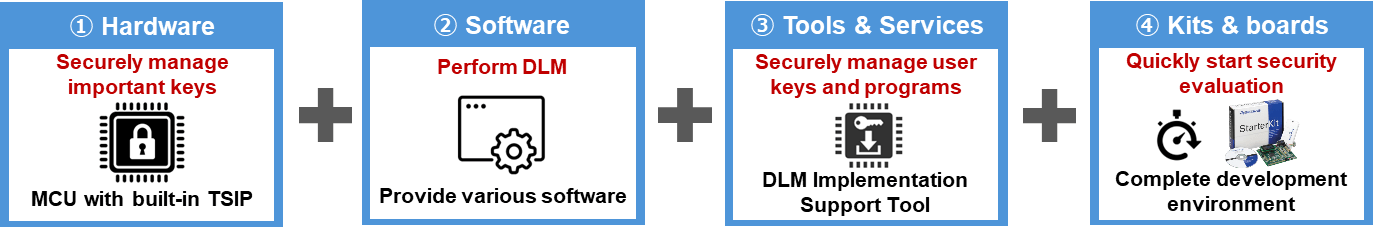
Hardware: RX Microcontroller Equipped with TSIP to Protect Against Threats
RX is equipped with TSIP, which cannot be accessed externally. Key data and the cryptographic engine in TSIP are strongly protected. Also, it safeguards user programs from tampering by leveraging RX-specific memory protection features like Area Protection and ID Code Protect. With this, you can build a system with Root of Trust that provides self-sustaining security and provides easy and robust protection from a variety of threats.
Advantages of MCU with built-in TSIP

Microcontrollers with TSIP
| On-board IP Function Comparison | TSIP-Lite | TSIP | ||
|---|---|---|---|---|
| Supported RX MCU | RX200 | RX231 RX23W RX26T | — | |
| RX600 | RX66T | RX651 RX65N RX671 RX66N | ||
| RX700 | RX72T | RX72N RX72M | ||
| Basic Functions | Common Key Encryption | AES (128/256): ECB / CBC / CTR | AES (128/256): ECB / CBC / CTR | |
| — | TDES (56/56x2/56x3): ECB/CBC | |||
| Public Key Encryption | — | RSA (1024/2048): Encryption/Decryption Signature generation/Signature verification Key generation (1024/2048) ECC (p-192/224/256): Signature generation/Signature verification Key generation (192/224/256) | ||
| Hash | — | SHA-1, SHA-256, MD5 | ||
| Authenticated Encryption with Associated Data (AEAD) | AES-GCM, AES-CCM | AES-GCM, AES-CCM | ||
| Message Authentication | CMAC (AES), GMAC | CMAC (AES), GMAC, HMAC | ||
| Random Number Generator | Random number generator (SP800-90A compliant) | Random number generator (SP800-90A compliant) | ||
| Key Update Function | AES key update | Key update for AES, TDES, RSA, ECC, HMAC key update | ||
| Key Exchange | — | ECDH | ||
| SSL/TLS Integration Function | — | SSL/TLS support function (TLS1.2, TLS1.3 compliant) | ||
Software
We provide you with the drivers that make TSIP work, as well as secure update and secure boot sample programs to use the RX-specific features so you can deploy security quickly and easily.
| Software Components | Description |
|---|---|
| TSIP Driver | Write keys and firmware to a dedicated driver that runs TSIP for the microcontroller |
| Secure Updating | A sample program that provides tamper detection/prevention by authentication when updating a program (Included in TSIP driver package) |
| Secure Boot | A sample program that prevents hijacking by detecting tampering during program execution (stops execution) (Included in TSIP driver package) |
Tools & Services
Renesas offers tools and services to support secure key operations throughout the device lifecycle, including key generation, key injection, and updating.
| Title | Description |
|---|---|
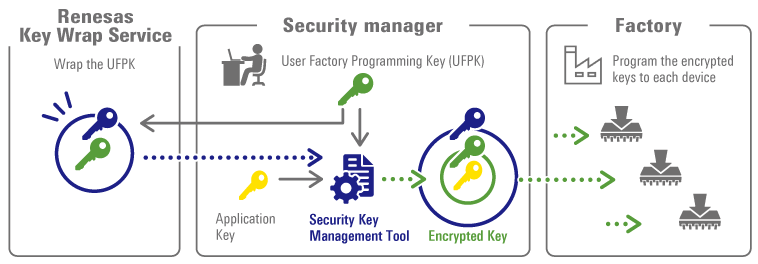
| Security Key Management Tool | A key wrapping tool supporting Renesas' security engine-based key management system, enabling secure key injection and updates for user applications and device lifecycle management (DLM). |
| Renesas Key Wrap Service | A service for securely wrapping keys via Renesas' dedicated web page and safely distributing them to devices and systems. |
Example of using the Security Key Management Tool during secure key installation
Evaluation Kits: TSIP Ready Evaluation Kits
Renesas offers evaluation kits that allow you to evaluate robust security immediately, contributing to reducing the turn-around time (TAT) for development of security-enabled devices. An NDA is not required for the manual and driver for Trusted Secure IP.
TSIP Ready Evaluation Kits
| Renesas Starter Kits | Envision Kit | Evaluation Kit | Cloud Kit | |
|---|---|---|---|---|
| Supported MCU | RX231 RX66T RX72T RX65N RX671 RX72N RX72M | RX72N | RX671 | RX65N |
| Features | Renesas evaluation kits that enable you to evaluate the full functionality of the MCU | Ideal for evaluation of HMI and security functions. Built-in debugger. | Evaluation kit that enables you to evaluate a combination of MCU features and common ecosystem add-ons. | An evaluation kit that enables cloud connectivity. TLS evaluation using TSIP is possible. |
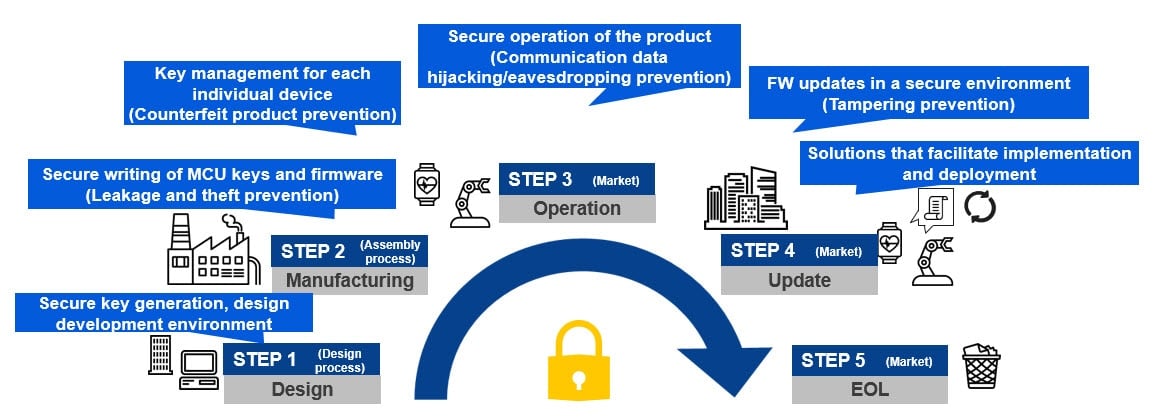
Achieving DLM with RX Security Solutions
There are various threats during the lifecycle of a user's product. You need not only security features for the device, but also secure operations throughout the lifecycle to respond to these threats. This way of thinking is called Device Lifecycle Management (DLM). RX security solutions support DLM and also make robust and advanced security management from the product lifecycle operation aspect possible.
Partners
Provides Trusted Secure IP enabled SSL/TLS
Enables differentiated software security features on the RX100 MCU Series
Certification
General-Purpose MCUs that Comply with International Security Standards
RX microcontrollers with TSIP are robust and reliable general purpose microcontrollers with NIST*2 FIPS*3 140-2 Level 3 CMVP certification applicable to HSM*1 and card readers. Also, each of the cryptographic algorithms in the TSIP is CAVP certified, so they can be used with confidence.
*1. HSM: Hardware Security Module
*2. NIST: National Institute of Standards and Technology
*3. FIPS: Federal Information Processing Standards
CMVP: Cryptographic Module Validation Program
A program that verifies that the FIPS 140-2 requirements are met
CMVP Certification with RX65N (2MB Devices)
| Certificate #3849 | |
|---|---|
| Module Name | RX65N-2MB Security Management Module |
| Standard | FIPS 140-2 |
| Overall Level | 3 |
| Module Type | Hardware |
| Embodiment | Single Chip |
CAVP: Cryptographic Algorithm Validation Program
A program that verifies that the algorithms approved for FIPS 140 are implemented correctly
CAVP Certified Cryptographic Functions (Cryptography in TSIP)
| Cryptographic Algorithm | Validation Number | Operating Environment |
|---|---|---|
| AES | A988 | TSIP |
| RSA | A988 | TSIP |
| ECDSA | A988 | TSIP |
| KAS (ECDH) | A988 | TSIP |
| SHS | A988 | TSIP |
| HMAC | A988 | TSIP |
| DRBG | A988 | TSIP |
| AES | A987 | TSIP-Lite |
| DRBG | A987 | TSIP-Lite |
Videos
Sixth in the RX security video series – Renesas walks through the process of encrypting the application program and performing a Secure Firmware Update using the Renesas Secure Flash Programmer so that the plain text of the application program to be updated is not exposed when updating the application program.
News & Blog Posts
Blog Post Sep 12, 2023 |
Blog Post Sep 11, 2023 |
Blog Post Jun 1, 2023 |
Blog Post May 19, 2023 |
Blog Post Apr 18, 2023 |
Blog Post Jun 27, 2022 |
Blog Post Mar 11, 2022 |
Blog Post May 19, 2021 |
Blog Post Apr 20, 2021 |
Blog Post Feb 18, 2021 |






