Recent news stories report that some fast chargers designed with MCUs can be easily hacked. When users connect their devices to these fast chargers via the USB cable, hackers may be able to compromise the charger by sourcing more power than the device can safely handle, damaging or even destroying the device. Hackers can alter the firmware of fast-charge devices in order to deliver extra voltage and damage connected equipment.
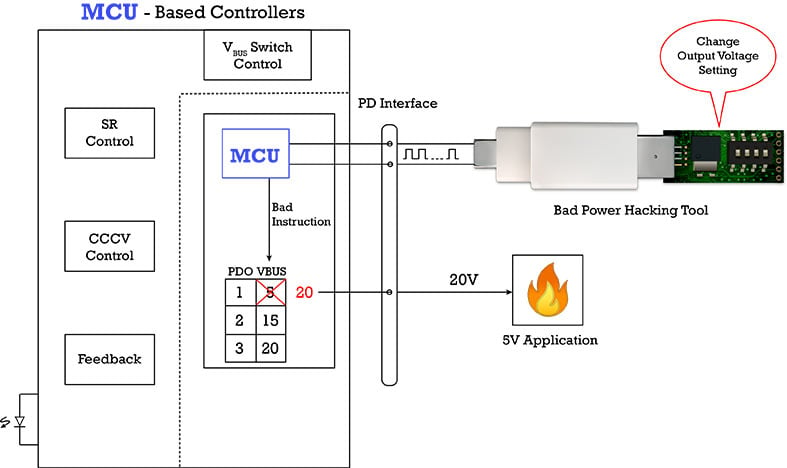
Designers can try to add more code in the MCU to prevent hacker modifications, but only if the MCU has the option to be updated. Or, they can try to add overload protections in the devices for which the chargers are designed. These methods are hardly ideal.
Hard-Wired State Machine Approach
A simpler and lower cost approach is to design fast chargers and power supplies without MCUs and firmware, and instead use a hard-wired state machine approach.
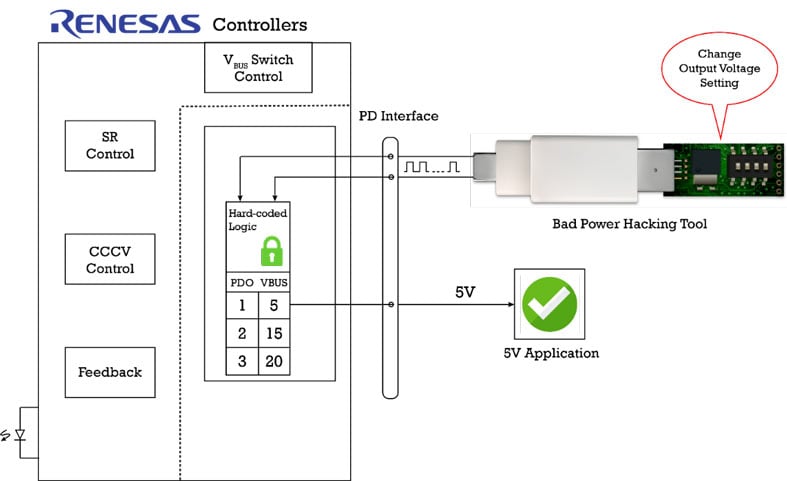
Fast chargers and power supplies designed with Renesas' Rapid Charge™ controllers cannot be hacked, because they are hard-wired state machines, so there is no firmware that can be accessed and corrupted. And, with a hard-wired state machine, you won’t need to spend extra time and expense to harden firmware or add overload protections.
All of Renesas' Rapid Charge™ controllers are hard-wired state machines.