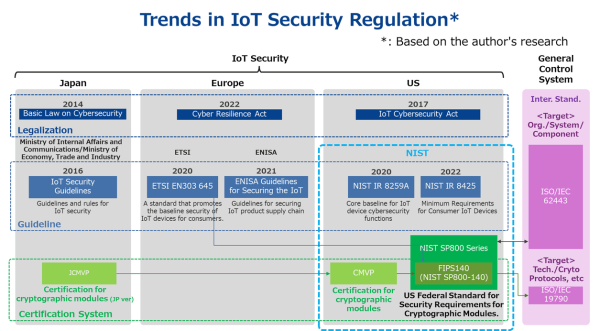
In recent years, the widespread use of IoT devices has led to a significant increase in cyberattacks. These attacks have the potential to cause major disruptions to socioeconomic activities and even threaten national security. As a result, countries around the world are working to establish security measures by enacting legislation and developing guidelines related to cybersecurity.
Recently garnering attention, the Cyber Resilience Act, which imposes new security requirements on digital products, has been announced in Europe. This legislation is anticipated to extend to everyday household appliances and other devices, so it's crucial to keep a close eye on its progression. In Japan, IoT security guidelines were put into place in 2017, while in the United States, the NIST IR 8259 was established to outline fundamental security requirements for IoT devices. Adhering to these guidelines is becoming more and more essential in today's world.
Amid the multitude of security requirements that have emerged, many of you may be struggling with determining the specific security measures that need to be implemented for your IoT devices.
As an international security standard that has been established for a long time, the standard model called FIPS140 has been defined by the NIST (National Institute of Standards and Technology) of the United States. FIPS140 defines how encryption modules should be developed according to the requirements of the US Federal Government, and a certification system (CMVP) has also been established.
Looking at the security requirements that each country has established, we can see that they are similar to the standard model defined by NIST in the following areas:
- Protection of highly confidential security parameters and personal data
- Root of Trust (a configuration element to verify device trustworthiness - secure boot, firmware update, tamper detection, etc.)
- Lifecycle management (key generation to use/disposal, etc.)
In other words, preparing for these similar requirements is a top priority for effective security measures.
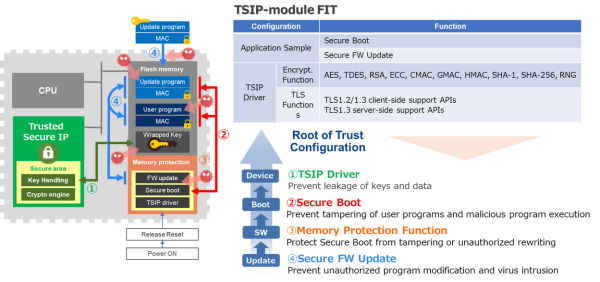
At Renesas, we focus on the NIST standard model and have implemented "Robust Key Protection", "Root of Trust", and "Secure Key Management" with our RX microcontrollers equipped with our proprietary security IP, Trusted Secure IP.
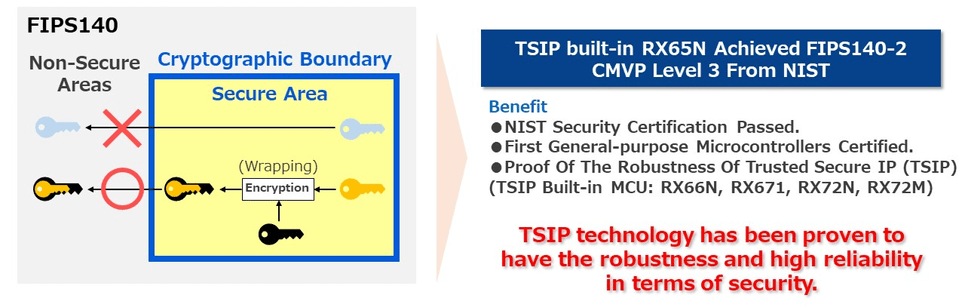
Of course, each country's security guidelines include the need to establish system-level measures and organizational structures, and it is not possible to cover all security requirements with semiconductor devices alone. However, RX microcontrollers with Trusted Secure IP do have features that cover the baseline security requirements and have achieved the highest level of CMVP Level 3, which is typically the highest level for consumer-level devices.
As mentioned earlier, one of the most critical tasks to prioritize is the establishment of a Root of Trust, which verifies the trustworthiness of software running on a reliable device. For attackers, the software is an excellent target to embed malicious code, making it vulnerable to attacks. With Trusted Secure IP (TSIP) integrated into RX microcontrollers, our security solution offers a comprehensive package of three software samples, including security drivers, secure boot, and secure firmware update. This one-package solution reduces the barriers to security implementation, allowing for the establishment of a Root of Trust and safeguarding customer assets from various threats.
As you can see, with just one RX microcontroller and three software solutions, we can achieve the Root of Trust, which is one of the top priorities. In addition, we offer various solutions for "confidentiality protection for security parameters and personal data" and "lifecycle management" on RX, so in the next article, we will touch upon those topics as well.